Multi-Factor Authentication and IT Security in 2018
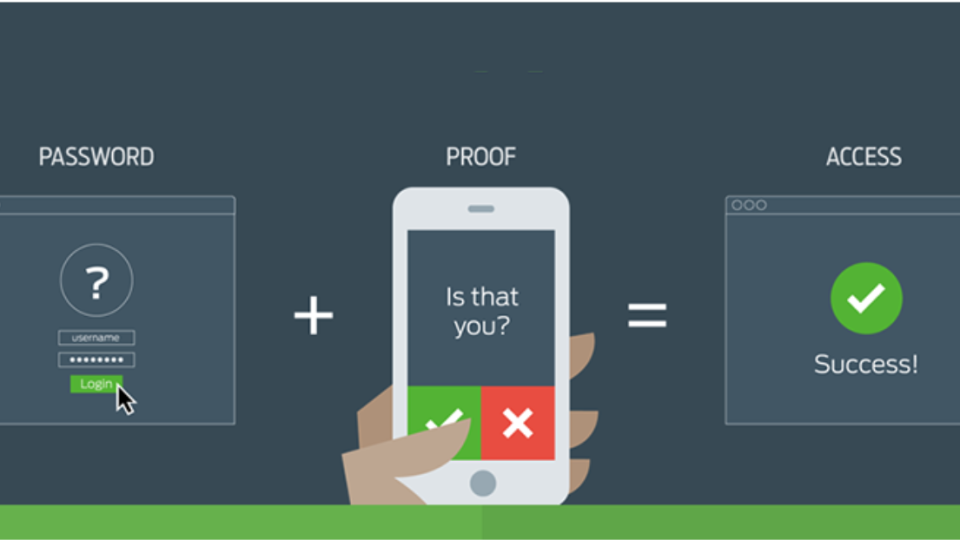
If you’re a tech geek like we are, you may have noticed an uptick in news about multi-factor (MFA) or 2-factor authentication (2FA) lately. From Google’s triumph over spear-phishers to Cisco’s intended acquisition of MFA unicorn Duo, there’s a lot of buzz around the security technology these days. So, what’s the deal with MFA?
Gone Ph
76% of businesses were reportedly victims of phishing attacks in 2017, and with almost 1.5 million new phishing sites being created every month, we only expect that number to rise in 2018. So, what exactly is phishing? This type of attack comes in two flavors: regular phishing and spear-phishing.
Regular phishing is a broader, catch-all approach. Scammers will usually impersonate a person or company (think your business’ CEO, a customer or vendor’s contact, or a provider like Gmail or Outlook) by either gaining access to that entity’s email account directly or creating a fake email account with a very similar name or domain (ex. [email protected] or [email protected]). They use this impersonated account to send phishing emails en masse to every address they can get their hands on. Generally, these emails will appear to be legit, and often include a link to a login page or form that looks almost identical to a trusted site. Unsuspecting recipients will click on the link and, unless they’re very attentive, will input their credentials or other important information into the phony form / login page. Once that happens, their information is compromised — in the hands of the phisher.
Spear-phishing uses the same basic concept but is a more targeted approach. The spear-phishing scammer will seek out one person or group of people at a certain organization and personalize the phishing email, leading to much higher open and click rates. Targeted individuals are usually in high-value or sensitive positions (CEO, security officer, accountant, etc.), so compromising them can cause a lot of damage to their organization.
MFA to the Rescue
Phishing attacks are only getting more sophisticated and more difficult to combat with attentiveness alone. Many users will understandably be tricked by familiar-looking login pages and email links from known and trusted contacts (how often do you verify the URL of the site you’re logging into?). This is where multi-factor authentication comes in. Depending on what type of MFA you’re using, you’ll need to accept a prompt, input a one-time code, or insert a security key after you provide your credentials to access any given resource. So, even if you do provide the correct credentials to the scammers, they won’t be able to access your account because they don’t have access to the device you use to service MFA prompts. In short, MFA provides an extra layer of security that can thwart many attacks.
Types of MFA:
Single-use SMS code
This type of MFA is probably the most common, and one you’ve probably run into before. Many websites or services will ask for your cell phone number when you create an account and send a text message with a code to that number to verify your identity. This method has come under fire lately because scammers can use SMS-intercept tactics to intercept the code if they know your phone number. See Reddit’s recent hack for a real-world example.
Authenticator app
Next up is the app-based authentication method. You may have used this with the Google Authenticator or Duo application. Users install an app on their cell phone which is then connected to their product / service that uses MFA (usually using a scanned QR code). The app generates timed codes to be used for MFA. This is more secure since there’s no SMS code being sent. An attacker would need to physically possess the targeted user’s cell phone and know their phone password to access the keys. This is the method we use at Propel.
Physical security keys
Mostly used by business banking outfits in the past, this method has been gaining popularity in more markets of late. Users are provided with a physical security key that they plug into their computer which authenticates logins for them. This is very secure, but not widely supported yet. We expect that to change in the near future given the events mentioned in this post’s intro paragraph.
Hopefully we’ve cleared up some of the mystery around MFA! If you have any questions or are interested in implementing MFA for your organization, please feel free to drop us a line at [email protected] or give us a ring at (720) 310-7620. If you’re ready to take charge of your organization’s IT, know that our Managed Services plan includes app-based MFA for every one of your users!
Stay Geeky, Folks
James
Sign up for the Propel Technology Blog newsletter
